How to Protect Your Business from Russian Cyber Attacks

Cyber breaches by Russian hackers are multiplying with each passing year, targeting small and big businesses worldwide. However, now that there are tensions between Russia and Ukraine, the world has become more cautious about its online defenses against the Russian cyber attacks. The United States Cybersecurity and Infrastructure Security Agency (CISA) has warned the nation to stay safe from Russian cyber warfare and take necessary steps to ensure complete online safety.
Recent research analysis from BBC has declared that about 74% of the online ransomware amount collected by attackers was directly linked to hackers in Russia. The report also stated that active hacker groups in Russia received about $400 million in crypto-currency in their accounts last year. Although Russia denies being involved in these cyber attacks, many researchers claim that Russian hackers are using crypto-currency for money transfers in and out of the country and therefore cannot be traced.
As per Microsoft, in 2021, about 58% of entire online attacks detected were linked directly to Russia. Attacks from Russian hackers are on the rise as the rate of successful compromise has gone to 32% from last year's 21%. Government websites and other branches are the primary targets as the attack rate on government agencies went from 3% to 53% in just one year. The government has advised every individual to properly check their data and accounts and carry out prevention methods for cyber attacks.
History of Russian hackers in the US
From 2009 to 2019, about 19 countries reported that they were attacked online from servers linking back to Russia. The USA as the main target was attacked alongside other EU countries. In July 2021, the Trump administration recognized that Russian hackers broke into critical government networks, including the treasury and commerce department. Unfortunately, hackers got their hands on all emails and systems from the office. This counted as one of the most structured and significant attacks on national accounts and systems in the past five years. The government officials said they started a hunt to determine if other areas of the government websites or accounts were compromised. Many officials also stated that some members of the national assembly were also getting targeted, making it more apparent that the plan targeted classified documents that Russian hackers wanted to get their hands on.
Types of cyber attacks
A cyber attack is an online attempt to breach your computer or any other IT device by an individual or organization without your knowledge. Usually, there is a motive behind such attacks which mainly comes down to asking for money from the victim.
Many types of cyber attacks can happen, but most of them are pretty simple in terms of understanding; let’s look at some of the widespread cyber attacks:
1. Malware Attack
Have you ever seen an online popup asking to speed up your computer by installing simple software? If yes then you might have encountered malware! When you click on it for downloading, the coding behind that virus will try to breach the network and get hold of your data or device. Therefore, it is advisable to never trust such popups and click on the links. There are many types of malware, including viruses, trojans, worms, etc.
2. Phishing Attack
This type of attack is usually done by faking a credible source. If you have received an email from a well-known company about clicking the link to install new software, never open it! These attacks aim to access your sensitive data (credit card and other login details) and steal heavy amounts or demand money from the victim against leaking the data.
3. Distributed Denial of Service Attack
Also known as DDOS, this attack sends a huge volume of fake traffic to a particular server or network, ensuring that existing bandwidth gets exhausted. The system, as a result, crashes and becomes unresponsive. At the same time, the attackers demand money from the victim to take back the traffic volume and let the service or network breathe.
4. SQL Injection
In this type of cyber attack, the attacker adds some malicious code to the comment section on the victim’s website. This code gets installed to the SQL and forces it to unlock any confidential document or information that could later be used by the attacker to threaten or blackmail the website owner.
5. Man-In-the-Middle (MitM) Attack
This is a new type of attack being carried out primarily on eCommerce platforms. The attacker intercepts the transaction of both buyer and seller and switches the transaction mode to steal the money. Such attacks are mostly made when the victim uses an insecure internet connection.
You are experiencing a cyber attack - What to do?
If you suspect your system security has been compromised, here are a few simple steps that you can take to control the damages:
-
The first thing is to isolate the network or system you believe is affected by the attack.
-
If you’re not sure which system was attacked, shut down the power from the entire system.
-
Meet the anti-virus team that may be able to help you.
-
Get a system image recorded of the device that was attacked.
-
Alert the relevant authorities of the law.
-
Start to repair the attacked system to restore the data loss.
-
Let your customers or other stakeholders know about the attack and the steps you are taking to ensure safety.
How to protect your business from potential cyber attacks?
If the hacker has not attacked you yet, these are some tips that you can follow to prevent your business from getting hacked. Let’s go through them one by one.
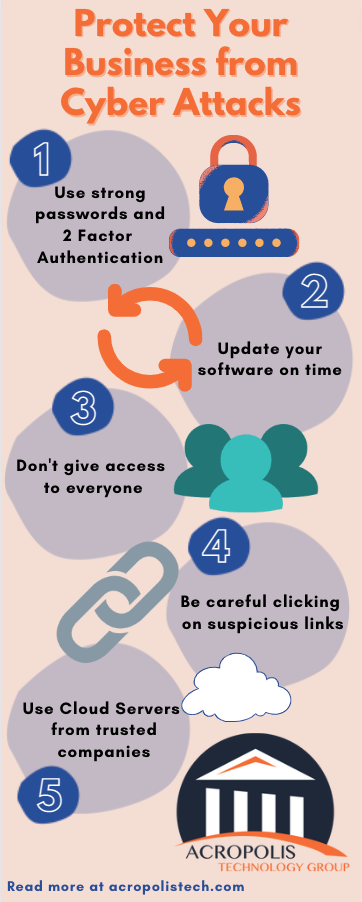
1. Use strong passwords:
Keeping a strong password will always be your first line of defense against any malware. To create a strong password, it's recommended that you avoid using any phrases or well-known words. Always include lowercase and uppercase letters along with symbols, and even numbers so that your password is hard to predict.
2. Two-factor authentication is a lifesaver:
The easiest way to prevent any potential risk of getting attacked by a hacker is to protect your account with two-factor authentication. It gives your account an extra layer of protection by letting you sign in after two steps. First, you get a pin code on your given email or text, once you try to sign in to the account. Once you paste that code only then does your sign-in process gets authenticated. The authentication app can perform all of these tasks efficiently.
3. Update your software on time:
You need to update your software or any device you are using continuously. Using the latest version on the platform is safer because the provider already secures the version against new attacks to ensure safety.
4. Don’t give access to everyone:
Make sure to know who is using your office systems. If many people have access to important files, anyone using your computer could click on faulty links resulting in information leaks to the hackers and creating problems for you. The key to staying safe is by restricting access control so that only trusted authorized persons could access confidential information.
5. Be careful about the links:
Did you know that businesses have encountered an 80% increase in phishing attacks in the last three years? That is why you must be well aware of what you are going to click and what is its source. Only click a link if you are sure that the person behind it is someone whom you know or if the link does not demand personal information such as bank details.
6. Use Cloud Server:
To protect yourself and even your customers, one step you can take is to limit the data type and the amount of data you are storing on the cloud server. Many services help you secure your information on the cloud and only utilize it whenever you need it. You need to ensure that an accounts department in your organization always uploads data to the cloud server on time. Also, use cloud servers only from a trusted and credible company.
Let’s Conclude
Russian hackers have been everywhere on the internet, and they are constantly targeting government websites. We must be prepared for the attack as Russia is trying hard to damage the world's economy. Due to the Ukraine war, the cyber attacks from Russia have gone down drastically, but we are well aware that it will not end here as the West is about to put more sanctions on Russia. Therefore, business owners must design and implement a cyber security plan that is solid and foolproof.
Cyber security is achievable through implementing new practices in the codes and ensuring that all software accounts are updated. The IT department should always check antivirus updates and other tools needed to control potential attacks. Lastly, if you’re into the consumer business, it would be great to let your customers know what information you collect and why when they visit your website or application. A good thumb rule is to never ask for social security number, bank account details, or other critical information from the consumer if it’s not necessary.
Gear up against Russian Hackers with the help of Acropolis
If you are worried about your company’s current security status, then contact Acropolis Technology Group at your earliest. We are a trusted managed security provider that can give you the best cybersecurity services for your company.
Written by: Adnan Ahmed
Contact us today!
